Cybergangs breaking into NBR server at will
On May 20, 2024, Chattogram Custom House Deputy Commissioner Mohammad Zakaria was in Kolkata, India, where he had gone for treatment a week earlier.
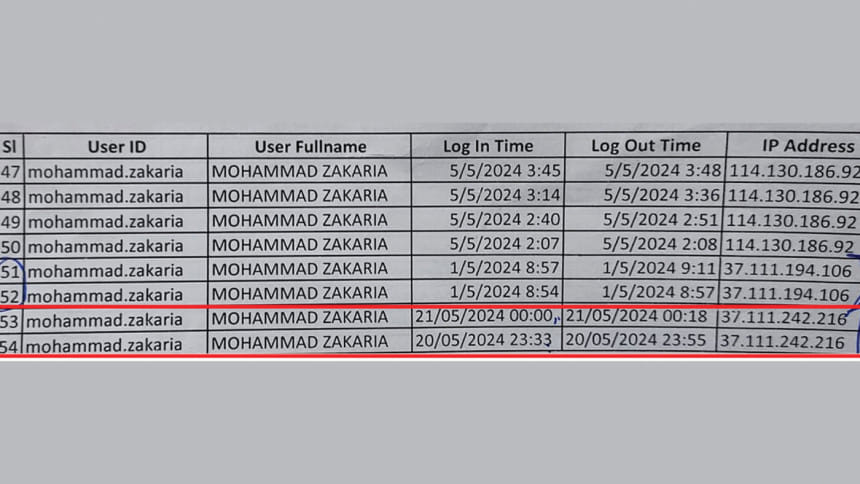
At 11:33pm that day, someone accessed the NBR server – Automated System for Custom Data (ASYCUDA) – using his ID and password. Just about half an hour later, the intruder logged in again, and completed the customs procedures for the release of a container of foreign cigarettes worth Tk 6 crore, imported through false declaration, customs investigators have found.
It was a highly sophisticated maneuver.
First, the imposter had to know Zakaria's ID and password to access the sensitive server. But even if they obtained or stole his security credentials, there were two additional security layers that needed to be bypassed, and the intruder bypassed both.
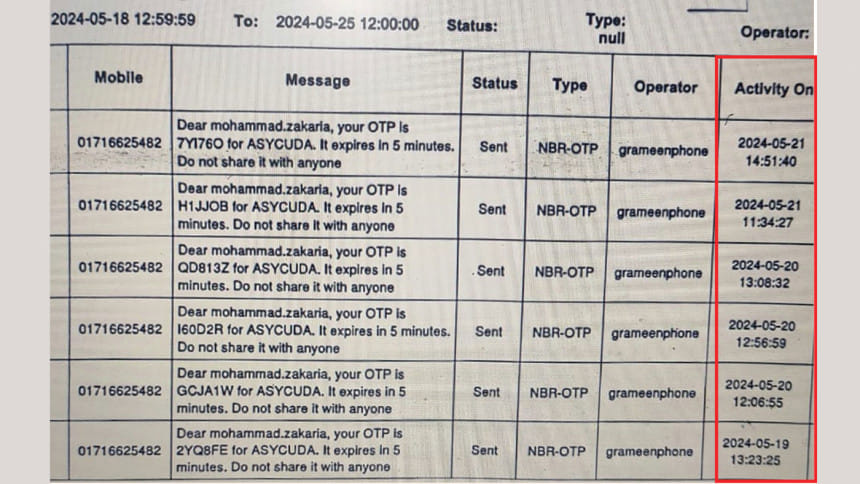
One of these two security layers involved mandatory generation of an OTP (One-time Password) that is automatically sent by the system to the ID holder's mobile phone. Ideally, the server cannot be accessed without that OTP, a crucial part of the system's multi-factor authentication to defend against security threats.
But Zakaria did not receive any OTP during the period, according to NBR's system-generated OTP report obtained by The Daily Star.

But consider this: the ASYCUDA user ID and password are device-specific and IP-specific, meaning even the authorised users cannot access the system from any other device or using any other IP (internet protocol). In this case, Zakaria's account was taken over from Bhandaria upazila of Pirojpur district using a different device and a different IP, device tracking record shows.
Customs officials eventually halted the release of the illegal cigarettes imported in the name of battery company Hamko, but the security breach has raised alarm among customs and NBR officials.
They described it as a "serious national security threat" because such unauthorised access at will means anyone is able to import or export any types and numbers of goods evading the customs process.
On October 22, NBR authorities formed a seven-member committee to get to the bottom of the intrusion.
In its written response to the customs investigators, Hamko denied any involvement with the import. It said someone must have used the company's name to bring in the shipment.
The Daily Star could not contact the company for comment.

Mohammad Azhar Uddin, founder of TiCON System Limited that specialises in IT security, said when a server can be accessed through an unauthorised IP, it is obvious that the server is compromised.
"The system not generating OTPs at a particular time primarily indicates involvement of insiders. But what actually happened or is happening in this case cannot be determined unless the server is audited. Servers usually leave a footprint of all activities. The sooner it is audited, the easier it will be to track down any suspicious activities," he told The Daily Star.
Customs' primary investigation, led by Chattogram Custom House Commissioner Mohammad Faizur Rahman, has established involvement of four people, including the prime suspect who penetrated the NBR server from Bhandaria using mobile internet.
The man is Sheikh Shezan, 23, from Narail district. He has been arrested several times in the last few years over alleged theft of public data from government servers, including the NID server and land ministry web portal. Every time, he came out of prison on bail within months.
He could not be reached for comment as all the 10 mobile numbers registered with his NID were found switched off.
When he penetrated the NBR server from Bhandaria using Zakaria's ID and password, he used mobile internet of a private operator.
The Daily Star is not naming the operator because it has no part in the intrusion, but the operator confirmed to the customs authorities that the specific phone number used at the time was registered under Shezan's name and NID number. This newspaper has the confirmation letter.
NOT AN ISOLATED INCIDENT
Data from Chattogram Customs House and Customs Intelligence show cybercriminals breached the NBR server to release at least 48 imported consignments and showed fake exports to launder money through at least 3,000 consignments from January 2019 to September 2024.
The import value of the 48 consignments was only Tk 9.58 crore. Of the 48 shipments, 12 were seized and their declared value was Tk 1.26 crore. But upon inspections, customs officials found that the consignments carried cigarette and liquor worth Tk 124 crore (nearly 100 times), documents show.
The declared value of the export items was Tk 1,218 crore, none of which entered Bangladesh, customs data show.
The Daily Star has seen 21 probe reports in relation to these security breaches. None of the investigations was able to track down the gang.
However, those investigations found that the gangs used IDs and passwords of at least 27 customs officials to complete the import and export process. In some cases, security credentials of transferred, retired or even dead officials were used to access server known as ASYCUDA World System.
These are unrelated to the May 20 penetration by Shezan.
AN ORGANISED GANG
Between January and May this year, cyber criminals penetrated the NBR server at least 114 times using the IDs and passwords of Zakaria and Sonia Sarkar Liza, a revenue officer of Chattogram Custom House, to complete customs procedures for the release of two separate shipments.
Not all of these are linked to Shezan but, again, neither Zakaria nor Sonia received any OTPs in any of these 114 cases.
One of these shipments had arrived in Chattogram Port, and the gang managed to smuggle it out of the port on June 2 before the port authorities could intercept it. As a result, the content in that container could not be known, the customs investigation report said.
Customs documents show the consignment was imported in the name of Inox Industries, located in Mongla EPZ.
In its written response to the customs authorities, Inox Industries denied any involvement, and said they may have been a victim of identity theft. We could not contact the company for comment.
The other shipment, containing nearly 12 lakh litres of liquor worth about Tk 14 crore, was intercepted by customs officials on September 4.
In this case, the gang entered Sonia's office room late at night on January 14 and accessed the server from her computer three times from 2:06am to 2:17am and one more time at 9:14pm. She was not in the office in those hours and she did not receive any OTPs at the time, the customs investigation has found.

"Those in charge of security of the building at that time can tell who entered my office in those hours and used my computer," Sonia told The Daily Star.
The container came from China in the name of Supreme Smart Wear Ltd, a garment exporter, in the guise of fabrics.
The company denied any involvement with the import, and said some gangs may have used its name.
"I'm not sure how the products were imported under the name of my company, which was not even in operation at the time. I believe some NBR officials are a part of the cybergang and they release illicit goods," Anisur Rahman Sinha, managing director of Supreme Smart Wear Ltd, told The Daily Star.
'THE SYSTEM HAS FLAWS'
Several IT officials at the Custom House said the system has been designed in such a way that no one can access the server from undesignated devices and IPs, which are tied to each other. Also, no one is able to access the system without the auto-generated OTPs.
"Sadly, what we see here is that these security layers get relaxed at certain hours when the cybergang needs it," said an IT official, who spoke on condition of anonymity citing ongoing investigations.
NBR Programmer Golam Sarwar controls the server and generates user IDs for all officials. He also determines the access limit according to the position of the officials.
He declined to comment about how someone could access the server from undesignated devices and why the system stopped sending OTPs at some particular hours.
A senior customs official said they detected many instances of unauthorised access and security breach of the server in the past as well, but this is for the first time they have been able to gather evidence against at least four people, including Shezan.
This is also for the first time that customs officials have detected intrusion of the ASYCUDA with a device and an IP that have not been officially authorised.
"However, we still do not know the ultimate beneficiaries of these shipments," the official said.
Developed by the United Nations Conference on Trade and Development (UNCTAD), ASYCUDA is a customs management system and is now used in nearly 100 countries, mostly in Africa and Asia. The system is meant to help governments improve supply chain efficiency, reduce corruption, and increase public revenues.
Bangladesh started using the system in 1994 to manage import-export operations through online on a small scale. In 2013, it was launched in all custom houses in the country.
The two-layer security system was introduced in 2022 to make sure the system is protected against security threats.
Contacted, NBR Member (customs policy) Hossain Ahmed said, "Before 2022, there was no option for OTP and no specific IPs for specific devices. We then added these two layers. Cybergangs still being able to penetrate the server bypassing the security layers indicates that the system has flaws that are unknown to us," he said.
"We invested around Tk 300 crore to secure our server in the last few years, but our import-export data remain still unsecure. The new NBR chairman has taken the matter seriously and instructed us to identify the real culprits even if they are our officials."

 For all latest news, follow The Daily Star's Google News channel.
For all latest news, follow The Daily Star's Google News channel. 








Comments