Ransomware, the weapon wielded in cyber attacks
A software that demands a ransom was the weapon of choice used in a wave of unprecedented global cyber attacks Friday that affected 130,000 systems in more than 150 countries.
The attacks have raised questions about how this so-called ransomware works, and how to guard against it.
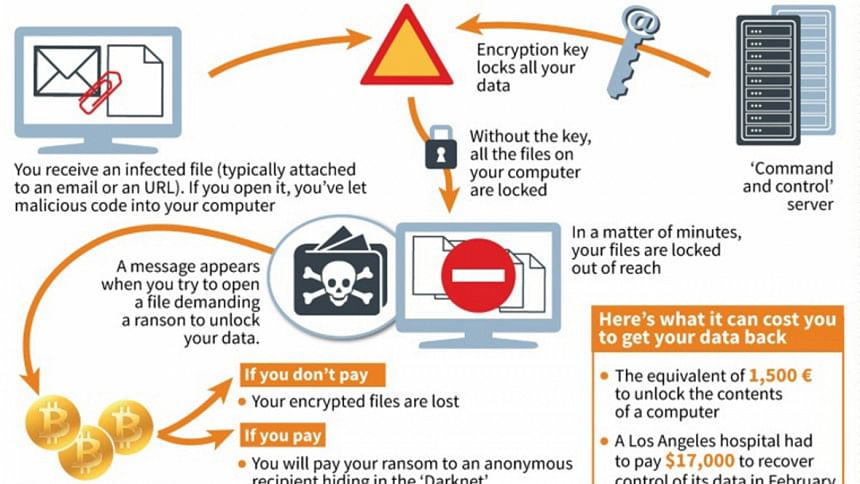
What is ransomware?
Ransomware is malicious software which locks computer files and forces users to pay the attackers a designated sum in the virtual Bitcoin currency to regain access to the files.
Ransomware is used on PCs as well as tablets and smartphones. It can affect "at the same time individuals, businesses and institutions," Amar Zendik, CEO security firm Mind Technologies, told AFP.
How does it work?
Cyber pirates generally take control of computers by exploiting flaws in the internet.
That could happen when a user logs onto a web site that has been previously infected or opens an email that invites the user to click on a link or download an attachment.
In a few seconds, the malware can be implanted. And when it's installed, "it can't be detected," Laurent Marechal, a cyber security expert at McAfee, told AFP.
It's only afterwards that it "downloads the 'payload', that is the viral charge," he said.
From then on the computer work station is blocked. "Most often the user has to send an SMS" -- and pay up -- "in order to get the unblocking code," says Marechal, adding that in certain complex cases, the virus can spread "without any human intervention".
Is it used frequently?
Yes. And ransomware continues to multiply. According to security software Kapersky Lab, 62 new types of ransomware were identified last year.
And the US computer security software company McAfee said the number of "samples" detected increased by 88 percent in 2016, totalling some four million.
"Often the pirates ask for small sums of money. But accumulated, these small amounts add up to big money," says cyber security expert Zendik.
Another expert Marechal said could be found on the 'dark web', an obscured part of the internet that's not indexed by classic search engines.
"Individuals can buy ransomware ready to use, sometimes only for $150," he said.
Why was Friday's attack so massive?
The culprits behind the cyber attacks apparently took advantage of a flaw in the Windows operating system, which had been divulged in documents leaked from the US National Security Agency (NSA), according to initial findings of the investigation.
Zendik said the attack was based on a previously unknown Windows flaw.
"We're not talking about classic 'ransomware' which generally targets individuals and small businesses," he said.
"Here the hackers attacked big institutions, not likely to be susceptible to paying, especially given the publicity about the operation."
He added that "in theory, the authors of the attack did not want to make money, but rather to achieve a (cyber) coup."
How can you protect against ransomware?
There are several simple rules that can be followed to reduce the risks of a ransomware attack.
Among them are regularly updating the computer's security software which can correct any flaws exploited by the virus.
In case of a cyber attack, the authorities advise disconnecting the infected equipment immediately from the network, in order to isolate them.
In the case of a virus affecting a business or an institution, the IT experts should be alerted right away.
Authorities also recommend not paying the hackers the ransom demanded -- because it's no guarantee that access to the data will be restored.

 For all latest news, follow The Daily Star's Google News channel.
For all latest news, follow The Daily Star's Google News channel. 



Comments