Need for better systems and protocols
The news that foreign hackers attempted to off $101 million from Bangladesh Bank's account with the Federal Reserve Bank of New York need not be viewed as a catastrophic failure; nor does it forebode disaster but it should give us some food for thought. It also is a wake-up call for the central bank, and calls for a transparent and diligent review process leading to an actionable plan to lower the chances of a repetition. In a recent piece in Prothom Alo, Dr. M. Farashuddin, former Governor of Bangladesh Bank, aptly points out that our central bank is the custodian of the nation's hard-earned money and it needs to guard it securely.
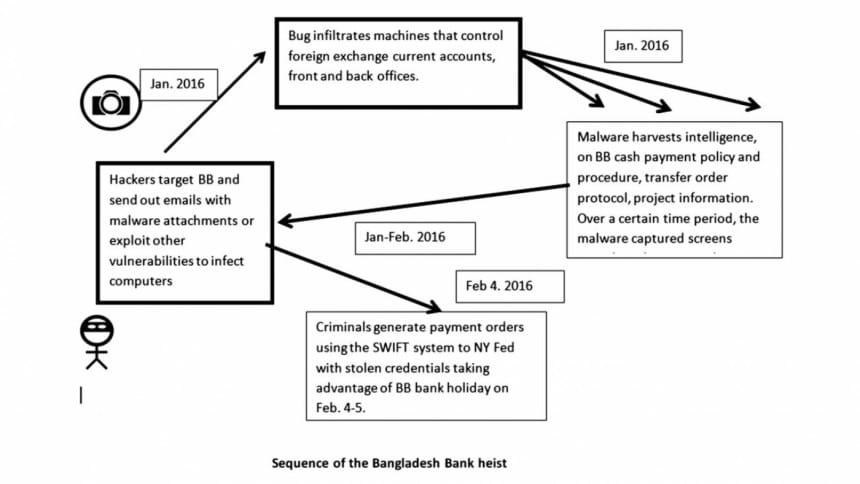
Bank heists in this day and age are not such a novelty, but what is worth noting is that from the information we have, it was carried out very efficiently and might have been executed by a gang of criminals working across four or more countries. The facts are well known. Bangladesh Bank (BB), which has been piling up foreign currency reserves in recent years, parks some of its foreign exchange reserves with the New York Fed. On or around February 4, 2016, BB apparently made several payments requests worth $101 million. These payment requests were processed and authenticated through SWIFT, an electronic communication channel utilised for financial transactions. Some of the money was transferred to accounts in the Philippines and Sri Lanka. The money laundering was detected the following week and BB officials and Bangladesh government have been successfully able to recover some of the funds, while it successfully froze others, and are in discussions with the NY Fed to get to the bottom of the whole episode.
The task before us, including government officials, central bankers, and cyber-security experts is to identify steps to prevent such occurrences in future and track down the criminals. Without getting too much into the technical details of this so-called "weekend caper", it appears that the criminals were able to crack the code that BB officials use, and decipher the practices that BB follows in authorising a transfer of funds from its account at the NY Fed, and bypass the checks and balances in place.
An operation of this cadre requires three steps: 1. Implantation of malware on the victim's computer system by taking advantage of a vulnerability or "back door". This is often done through "phishing," whereby emails are sent to targets which have attachments with malware; 2. Once the BB computers were hacked into, the criminals received regular information on bank protocols, transfer messages, passwords, and other authenticating keys; 3. The hackers then mimic the staff using stolen credentials.
It is a fair guess that hackers employed familiar methods, using phishing emails or other tricks to entice BB officials to lower their guards to download malware from emails. A few technical tools are widely available, and system administrators at any financial institution are on the alert against: Advanced Persistent Threats (APT), Spear Phish emails with exploits, financial crimeware, banking Trojans, and bots. The sophistication level of the hackers has reached new heights, and users need to be on the watch against MS Word and PDF attachments even from apparently known sources. Monitoring and virus disinfection routines plus regular software and hardware updates are standard practices in today's world. The forensic experts hired by BB need to examine existing protocols followed by the Forex Reserve and Treasury Department, and the Budget and Account Department and recommend state of the art practices from the world of computer and network security.
News accounts have identified three roles in initiating a transfer of the funds: the maker, checker and authoriser. The breach probably happened on one or multiple of these sources, and allowed the hackers to gain a good understanding of BB's internal workings. The modus operandi could be spying electronically on bank workers, identifying patterns in bank payment orders, and breaching the SWIFT protocol. The important takeaway is that such breaches are not 100 percent preventable but all measures available must be taken to minimise such risks. Experts recommend all financial organisations to carefully scan their networks for the presence of malware, and if detected, report the intrusion to law enforcement, both national and international. Incidentally, participants at a cyber security conference held last week in Washington, DC, and organised by the Homeland Security Department and the Secret Service, identified some key areas for improvement:
- Test human response and coordination in case of cyber attacks
- Ensure people have and follow protocols
- Allow security personnel to share information effectively
I can vouchsafe that all these measures are equally applicable to enhance the cyber security of our treasured foreign exchange reserves.
The writer is an economist and has been working in ICT for three decades.

 For all latest news, follow The Daily Star's Google News channel.
For all latest news, follow The Daily Star's Google News channel. 








Comments